Ethereum Cryptography Explained

Introduction to Ethereum Cryptography
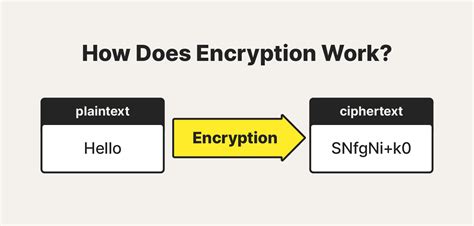
Ethereum, one of the most widely used blockchain platforms, relies heavily on cryptography to secure its network and enable secure transactions. Cryptography, in the context of Ethereum, is used to protect user data, ensure the integrity of transactions, and control the creation of new units. In this article, we will delve into the world of Ethereum cryptography, exploring its key concepts, mechanisms, and applications.
Key Concepts in Ethereum Cryptography

Before diving into the details of Ethereum cryptography, it’s essential to understand some key concepts: * Public-key cryptography: This is a method of encrypting data using a pair of keys, one public and one private. The public key is used to encrypt the data, while the private key is used to decrypt it. * Hash functions: These are one-way functions that take input data of any size and produce a fixed-size output, known as a hash or digest. Hash functions are used to verify the integrity of data and to create digital signatures. * Digital signatures: These are a type of asymmetric cryptography that uses a pair of keys to authenticate the sender of a message and ensure the integrity of the message.
Ethereum’s Cryptographic Mechanisms
Ethereum uses several cryptographic mechanisms to secure its network and enable secure transactions. These mechanisms include: * Elliptic Curve Digital Signature Algorithm (ECDSA): This is a type of digital signature algorithm that uses the elliptic curve discrete logarithm problem to provide a secure way of authenticating the sender of a message. * Keccak-256: This is a type of hash function that is used to verify the integrity of data and to create digital signatures. * AES: This is a type of symmetric-key encryption algorithm that is used to encrypt data.
Applications of Ethereum Cryptography

Ethereum cryptography has several applications, including: * Secure transactions: Cryptography is used to secure transactions on the Ethereum network, ensuring that funds are transferred correctly and that transactions are resistant to tampering. * Smart contract security: Cryptography is used to secure smart contracts, which are self-executing contracts with the terms of the agreement written directly into lines of code. * Wallet security: Cryptography is used to secure Ethereum wallets, which are used to store, send, and receive Ether (ETH) and other Ethereum-based assets.
How Ethereum Cryptography Works

Here’s a step-by-step overview of how Ethereum cryptography works: * Key generation: A user generates a pair of keys, one public and one private, using a cryptographic algorithm such as ECDSA. * Transaction creation: The user creates a transaction, which includes the recipient’s address, the amount of Ether to be transferred, and other relevant details. * Transaction signing: The user signs the transaction using their private key, creating a digital signature that verifies the sender’s identity and ensures the integrity of the transaction. * Transaction verification: The transaction is broadcast to the Ethereum network, where it is verified by nodes using the sender’s public key and the digital signature. * Block creation: A group of verified transactions is collected into a block, which is then added to the Ethereum blockchain.
🔒 Note: The security of Ethereum cryptography relies on the strength of the cryptographic algorithms and the secrecy of the private keys. Users must keep their private keys safe to prevent unauthorized access to their Ethereum accounts.
Benefits of Ethereum Cryptography

Ethereum cryptography provides several benefits, including: * Security: Cryptography ensures the secure transfer of funds and the integrity of transactions on the Ethereum network. * Transparency: Cryptography enables the creation of a transparent and tamper-proof record of all transactions on the Ethereum network. * Immutable: Cryptography ensures that the Ethereum blockchain is immutable, meaning that once a transaction is written to the blockchain, it cannot be altered or deleted.
Challenges and Limitations of Ethereum Cryptography
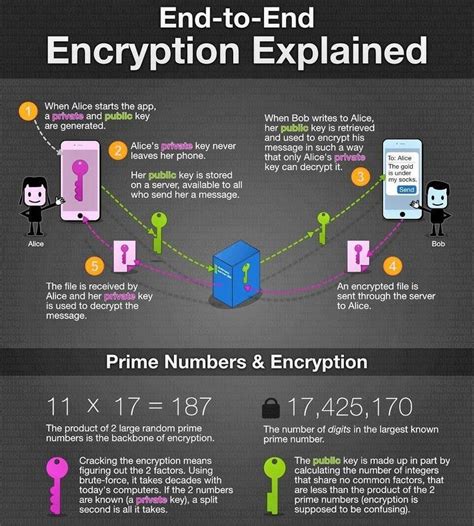
While Ethereum cryptography provides several benefits, it also faces several challenges and limitations, including: * Scalability: The use of cryptography can limit the scalability of the Ethereum network, as the creation and verification of digital signatures can be computationally intensive. * Quantum computing: The rise of quantum computing poses a threat to Ethereum cryptography, as quantum computers have the potential to break certain types of encryption. * Key management: The management of private keys is a challenge, as users must keep their keys safe to prevent unauthorized access to their Ethereum accounts.
Future of Ethereum Cryptography

The future of Ethereum cryptography is likely to involve the development of new cryptographic mechanisms and the improvement of existing ones. Some potential developments include: * Quantum-resistant cryptography: The development of cryptographic algorithms that are resistant to quantum computing attacks. * Homomorphic encryption: The development of cryptographic algorithms that enable computations to be performed on encrypted data. * Zero-knowledge proofs: The development of cryptographic algorithms that enable the verification of transactions without revealing sensitive information.
What is the main purpose of Ethereum cryptography?
+The main purpose of Ethereum cryptography is to secure the Ethereum network and enable secure transactions.
What type of cryptography does Ethereum use?
+Ethereum uses a combination of public-key cryptography, hash functions, and digital signatures to secure its network and enable secure transactions.
How does Ethereum cryptography ensure the integrity of transactions?
+Ethereum cryptography ensures the integrity of transactions by using digital signatures, which verify the sender's identity and ensure that the transaction has not been tampered with.
In summary, Ethereum cryptography plays a crucial role in securing the Ethereum network and enabling secure transactions. Its applications include secure transactions, smart contract security, and wallet security. While it faces several challenges and limitations, the development of new cryptographic mechanisms and the improvement of existing ones will help to address these issues and ensure the continued security and integrity of the Ethereum network. The future of Ethereum cryptography is likely to involve the development of quantum-resistant cryptography, homomorphic encryption, and zero-knowledge proofs, which will help to further enhance the security and functionality of the Ethereum network.


